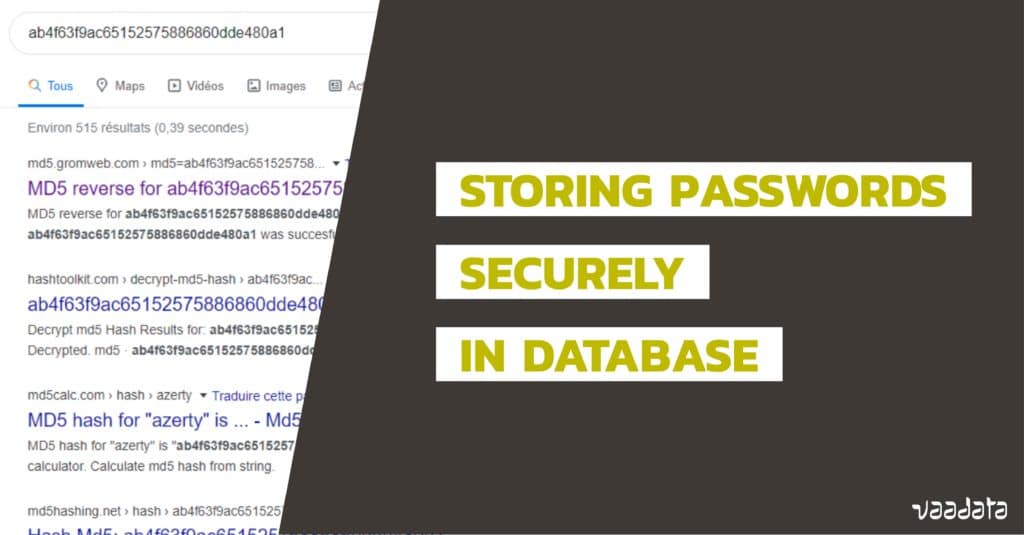
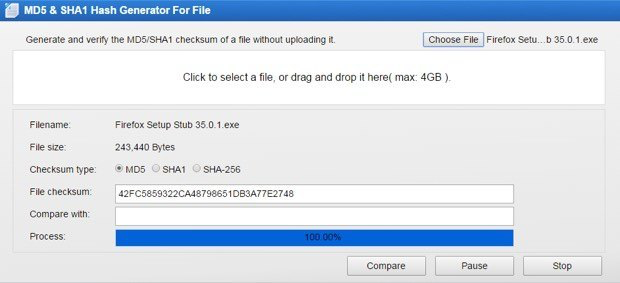
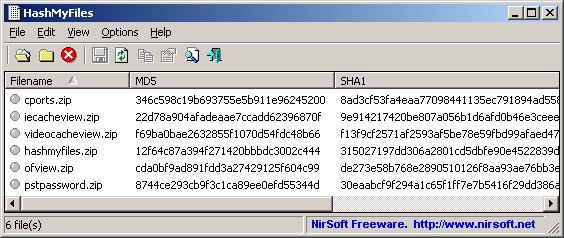
Integrating encryption techniques for secure data storage in the cloud - Seth - 2022 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
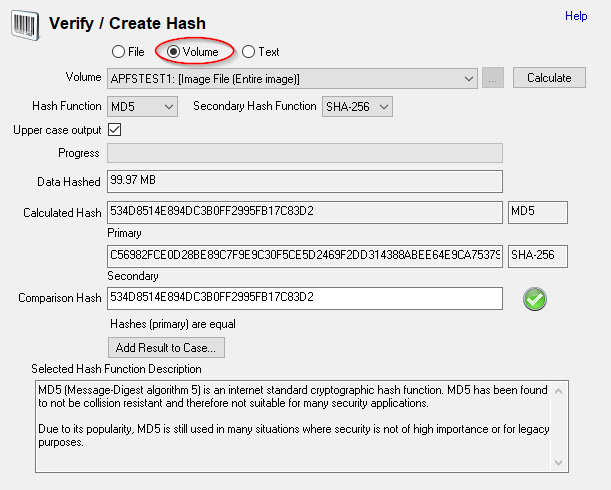
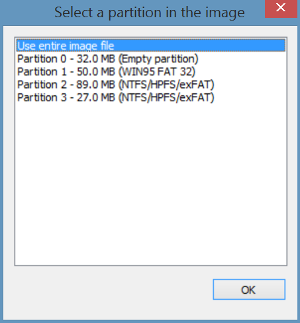
OSForensics - FAQs - How to check the MD5 (or SHA1) hash checksum of an entire volume, disk or image

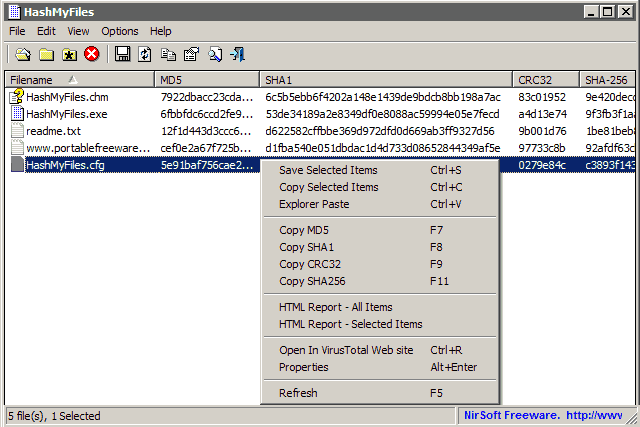
How do you determine the SHA-256 or SHA-512 checksum of a file? - ID: 109483101 - Industry Support Siemens
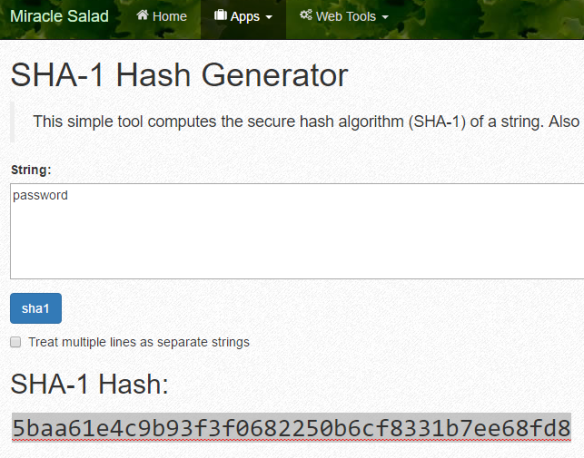
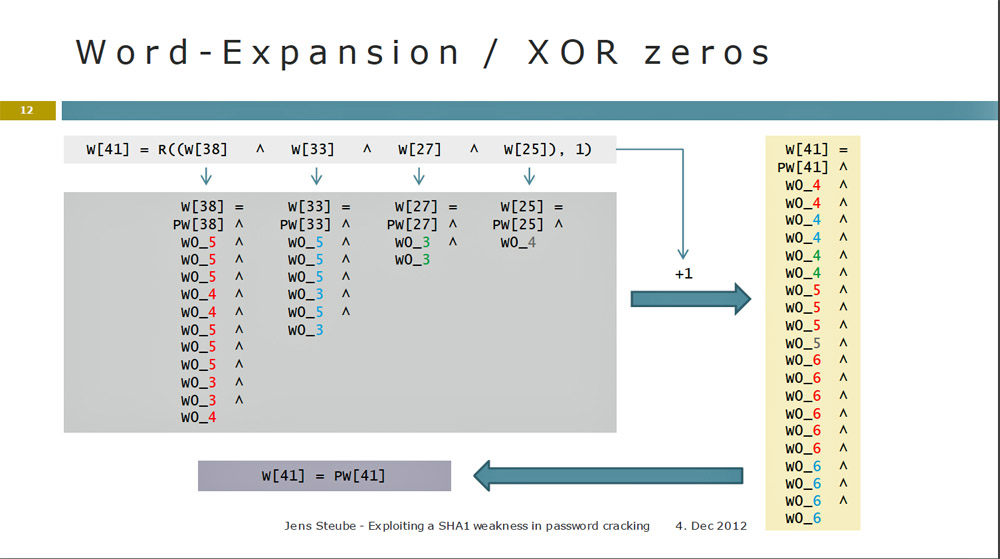
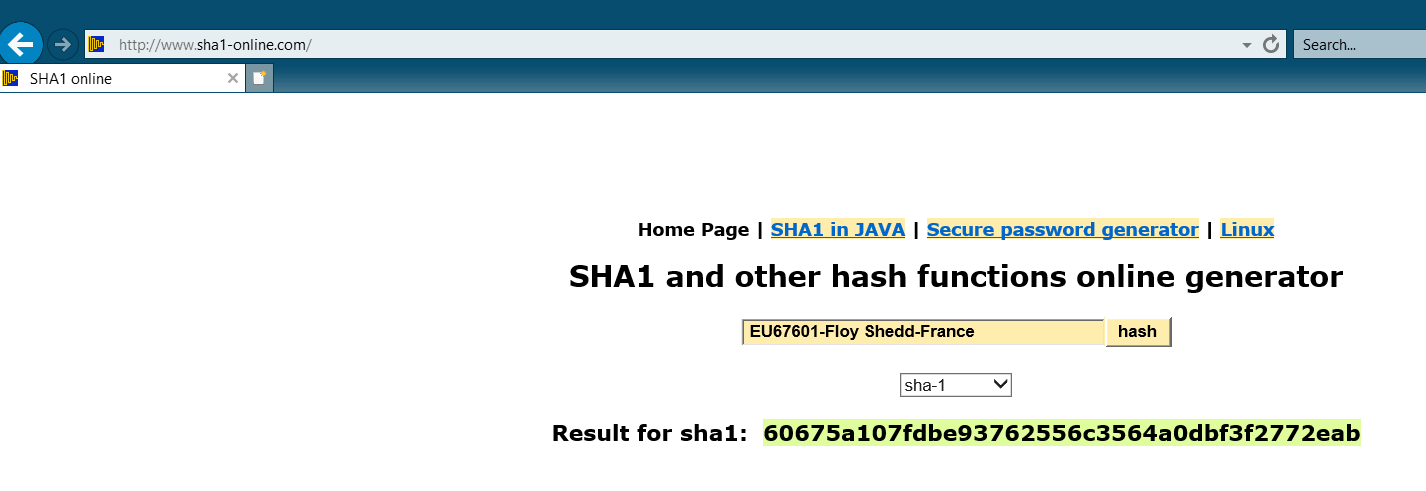
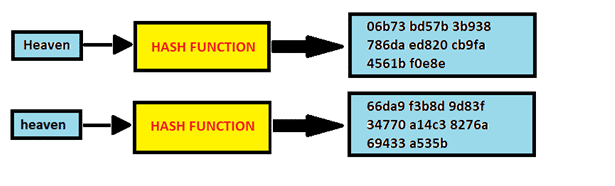
How to Crack SHA1 password hashes – online Crackstation – Visual guide | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021
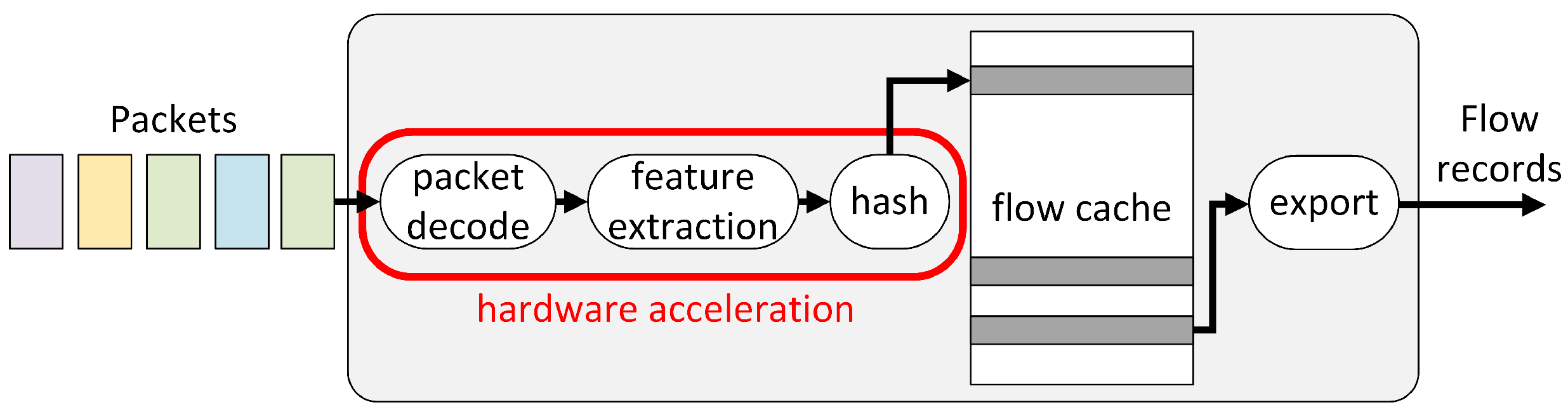
Electronics | Free Full-Text | Comparison of Hash Functions for Network Traffic Acquisition Using a Hardware-Accelerated Probe
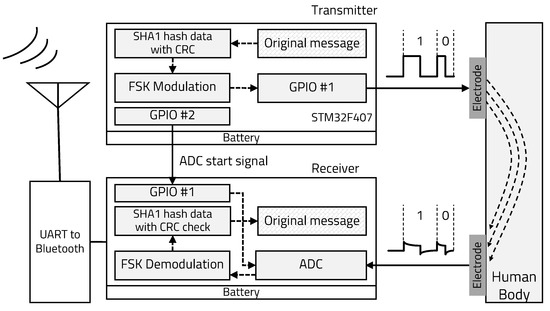
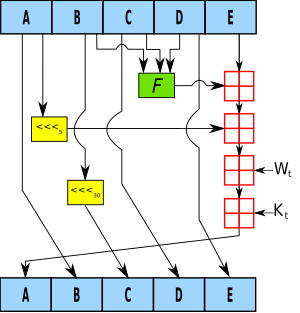
Sensors | Free Full-Text | Robust Intra-Body Communication Using SHA1-CRC Inversion-Based Protection and Error Correction for Securing Electronic Authentication